Safeguarding Your Online Security as an Individual
It is funny how a lot of people are vulnerable to cyber-assault when having their several online activities as a result of security loopholes created by them. It’s so bad that many are oblivious to it. This article would help us understand some of these loopholes and how to beef up our security online.
POSSIBLE SECURITY LOOPHOLES
- APPLICATIONS
- WEB PLATFORMS
- UNSOLICITED MAILS
APPLICATIONS
A lot of us don’t know how to secure our privacy whenever we get online. We just consume any content we come across without confirming what it is or verifying the source.
You know the interesting part, most of us don’t even read through the privacy/terms and conditions of the applications we use or web platforms we visit. We just accept them without reading because we want to get into the app or use their services already. 99.9% of us are guilty of this and I’m not exempt (statistics generated by me). Apparently, we all like to take the fast lane and no one wants to be slowed down by any form paperwork because it can be really tiresome.
So here’s what it is, we all have to be sensitive and be able to scrutinize what and who we allow access into our lives. In the real sense of it all, our privacy isn’t 100% certain on these apps and web platforms but we can make a deliberate effort to monitor what goes on under the hood.
UNSOLICITED MAILS
It is also important that we vet the mails we receive because not all might be useful. Over the years, I have been spammed by random people inviting me for one job interview or the other. Sometimes, I am been told I have won some money I did not know about somewhere. Yeah, it is that serious and these internet fraudsters really mean business. Unsolicited mails have been used by fraudsters to perpetrate cyber-crime. My advice to you is that you steer clear of such mails immediately you receive them so as to protect yourself from possible harm.
Here is an example of an unsolicited mail I got from some persons trying to clone a mail from Google mail support. On opening the mail, I already got a warning that such mail had been marked as spam by some other people that must have received it.
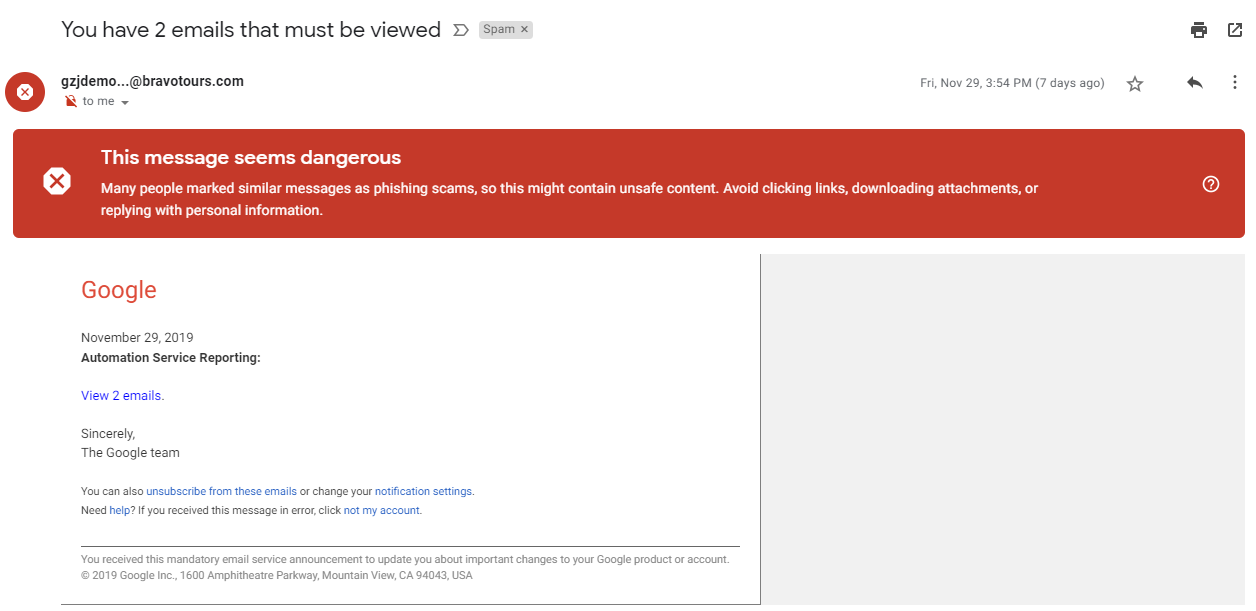
Also, I clicked the dropdown arrow to see more information on the sender details and I noticed that the sender was not a reliable.
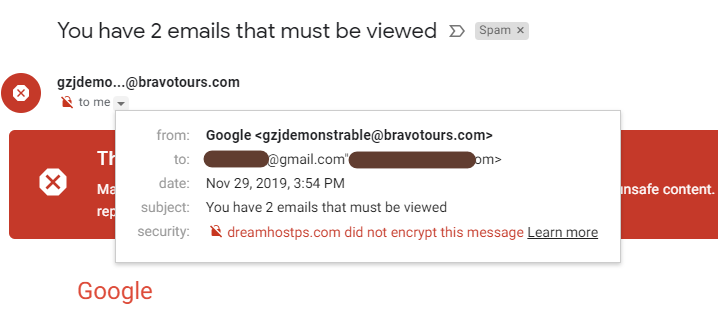
In terms of security, it can be seen that the message sent to me wasn’t encrypted. Thus, if I go through with responding to such mail, I am susceptible to being compromised.
HOW TO SAFEGUARD YOUR SECURITY ONLINE
- Use strong password
- Read terms and conditions (TOCs)
- Scrutinize links
MAKE USE OF STRONG PASSWORD:
One secure way to ensure that your activity online is safe is by using strong passwords that would make it very difficult to be hacked even when it is put under brute force account. Here are a few tips to strengthen you passwords:
- Avoid using passwords that are easy to guess.
- Avoid passwords that contain your name, birthdays or any other personal biodata.
- Make use of alphanumeric characters to generate a password. You can visit any of the following links to generate a strong password.
https://passwordsgenerator.net/ or https://identitysafe.norton.com/password-generator - Do not write down your password in a book or memo that can be easily accessed by any one.
- Avoid using the same password on all platforms.
- Most importantly, memorize your passwords and save them in your head as that is the most secure place to store them.
MAKE SURE TO READ THROUGH TERMS & CONDITIONS/PRIVACY POLICIES:
Yes you read that correctly. It might seem like a chore to read through paperwork comprising agreement, terms & condition and privacy policies but it is for the greater good as you would be duly informed on what you need to know regarding the codes and conduct governing an app or web platform.
Here’s a case study of what I experienced personally. It happened that I was in Labak Estate, Lagos for a few hours recently. I did not remember turning on my GPS but Google Maps had a way to detect my exact location and propagate my data without my knowledge.
Now you might be wondering how this came about. You see, Google Maps had been programmed to pick up data (sometimes offline data) for some reasons best known to Google. So it is possible my travel data was cached temporarily on my phone pending the time I got internet access then it sends the information to the appropriate quarters or my GPS was still working underneath since I was connected to the internet even after I deliberately turned it off.
I may be ranting that all this happened without my consent but really, what if it was stated somewhere in the terms and conditions of the app and I didn’t read it while I was activating it. That’s a possibility. I might have unconsciously authorized these data to taken from me while signing up or at some point of using the app and I was oblivious to it.
So, in this scenario Google Maps wasn’t used to perpetrate evil but just imagine if this data about you got into the hands of some evil mastermind and it was used in a devious way. You’re toast already.
For those of you that are familiar with the Invictus Saga, it will interest you to know that data was collected from platforms like Facebook and WhatsApp in order to track these guys so they could be apprehended.
Well I’m not trying to scare you or something but what do you have to lose really? Save you have something up your sleeves 😅. So think twice before you plan that sinister plot of yours.
Now you see nothing is completely private as it were. In the past, we have heard stories of how companies like Facebook and other internet giants have sold our user data without our consent.
Some of these platforms have a blog section and other resources they use in publishing regular updates about them and other changes. From time to time, check the updates to see if it goes well with you. If it doesn’t, make a run for it.
These developers can be very smart with just a line of legal jargon and you find out that you were outsmarted at the end of the day. You also have the responsibility of doing your own due diligence because ignorance isn’t really an excuse.
ALWAYS SCRUTINIZE LINKS:
Make it a habit of scrutinizing any link you come across before opening it because not all links are safe for you. Sometime trusted web platforms get clones by scammers and are used to collect sensitive user data from unknowing victims. In other to avoid falling victim to such, it is advisable to check properly to know these platforms are authentic.
A good way to confirm the authenticity of these platforms is by making sure you are on a secured page most especially when you are there to perform financial transactions. You can look out to confirm the platform has been issued a secured sockets layer (ssl) certificate which symbolizes trust and authenticity. The prefix of a platform with an ssl certificate would begin with https:// and not http://.
Any form of information sent over an ssl connection is encrypted and less susceptible to being compromised.
FOOD FOR THOUGHT
Be careful of who and, or what you let into your life as being safe online should be of utmost importance to you, your business and your sanity.

